How to Secure Digital Twin Technology in Your Data Center – Data Center Knowledge
Originally posted on techexec.com.au & datacenterknowledge.com
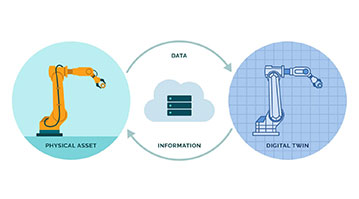
A compelling use case in the data center industry for digital twins is the inspection and maintenance of high-risk electrical equipment.
But a digital twin also multiplies any underlying security problems in a data center’s operational technology, provides attackers with a new avenue for attack, and can also give attackers unprecedented access into a data center’s operations.
To address these risks, data centers using digital twin technology should redouble efforts to ensure that they maintain security best practices in the underlying systems, strengthen access controls, and accelerate the transition to a zero trust architecture.
Risks of Digital Twins in Data Centers
Unauthorized access to digital twins can pose significant security risks, said Mahadeva Bisappa, principal architect at consulting firm SPR.
“Not only can a malicious actor gain access to the digital system it replicates, but also to its physical assets – which can be more dangerous,” he told Data Center Knowledge.
In addition, if a data center’s digital twin is compromised, the attackers may be able to gain access to the data stored in the data center.
The problem is that operational technology often lags behind when it comes to cybersecurity.
Legacy systems in particular are hard to secure.
Updates may not be readily available, said Matt Chiodi, chief trust officer at security company Cerby.
“If a digital twin is made of a physical system, any misconfigurations or vulnerabilities in that system are now doubled,” he said.
Without good asset and vulnerability management practices, a data center can exponentially increase the attack surface by deploying a digital twin — and can increase it exponentially if there are multiple twins.
“A vulnerability in one twin now is multiplied by the number of twins or copies,” he said.
Another security issue specific to digital twins is that they often draw on information collected by IoT devices, said Walt Greene, CEO of consulting firm QDEx Labs.
“Unfortunately, protecting these or any other small IoT device with serious security protocols is extremely difficult,” he said.
In other cases, data is collected from legacy sensors connected to physical machines in order to track how they’re performing in real time — and predict how they will perform in the future.
In the past, these sensors may not have been easily accessible from outside the data centers.
With a digital twin in place, this information is now more readily accessible.
“It does make existing systems and data flows more visible,” said Forrester vice president and analyst Paul Miller. “Security by obscurity was never a good defense, but solutions like digital twins make it nearly impossible going forward.”
Since it can be used to make changes to a device’s behavior from a remote location, a data twin can become an attractive attack vector, said Ben Kotvis, senior architect, consulting services at Insight.
“For example, a digital twin might contain a high-temperature threshold for a temperature sensor,” Kotvis said. “If someone was able to hack the digital twin and raise that threshold, it could take the data center down if the temperature is allowed to go high enough.”
Loop Digital Twins into Your Zero-Trust Framework
Since digital twins can expose and magnify any underlying security issues, the first step to securing digital twins is to secure the underlying environment.
This would be a good time to embark on a zero trust security program, if a data center hasn’t done so yet.
A zero-trust security framework requires all users – whether inside or outside an organization’s network – to be authenticated, authorized, and continuously validated at every stage of a digital interaction, said QDEx Labs’ Greene..
Adopting zero trust is the best way to secure digital twins, he said.
In addition, there are established best practices that are specific to digital twins, he said. “There’s a standard litany of cyber security hygiene for data centers involved with digital twinning.”
They include limiting access to services on an as-needed basis, and based on limited authorizations and permissions, keeping all patches up to date, using strong password controls and multi-factor authentication, and using secure, encrypted protocols where appropriate.